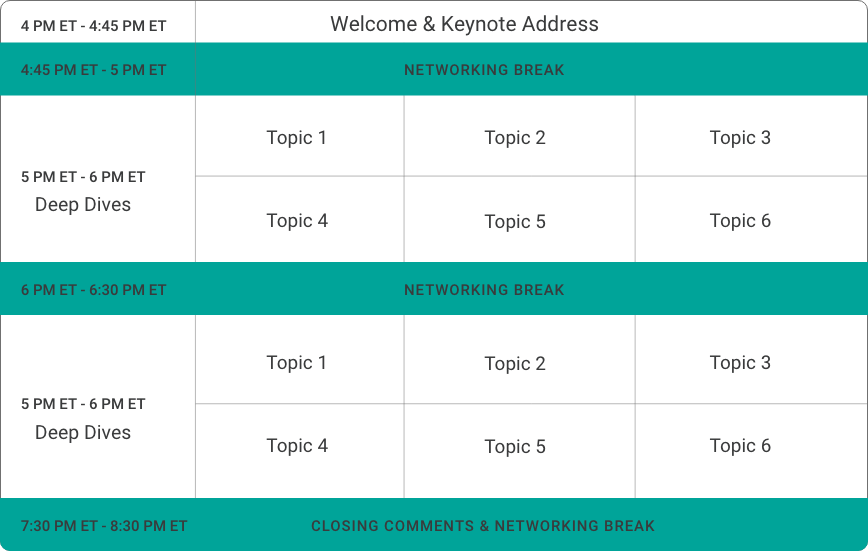
Deep Dive Topics
- A Deeper Look at the Current Threat Landscape
- How to Create a Secure Cloud Strategy
- Building Good Data Governance Standards
- Mitigating the Impact of Business Email Compromise
- AI Tools: What are the Cybersecurity Implications?
- Third Party Selection and Management
- Understanding the Cryptocurrency Space
- Incident Response: Are You Prepared?
SESSION FORMAT – Moderated by a security thought leader and foremost solution provider in a closed-door boardroom setting.