Deep Dive Topics
- Zero Trust
- OT
- Cybercrime
- Ransomware
- Fraud
SESSION FORMAT – Moderated by a security thought leader and foremost solution provider in a closed-door boardroom setting.
ISMG Engage Seattle addresses the challenges ahead that are constantly evolving and impacting every aspect of our business and personal lives. We will bring together industry leaders and decision-makers to connect and learn from each other’s success, as well as challenges, in an interactive educational environment.
NOTE: This in an invitation-only event and space is limited. All requests to attend will be reviewed by event staff and approved based on professional qualifications and event capacity.
SESSION FORMAT – Moderated by a security thought leader and foremost solution provider in a closed-door boardroom setting.
ISMG Engage brings the foremost thought leaders and educators in the security space to the stage and knowledge sharing discussions. Hear what is on the minds of leading security experts as they share insights and challenges of the ever-evolving threat landscape.
In this engaging keynote session, we will take a fresh approach to discussing advancements in artificial Intelligence and machine learning by combining a traditional panel format with an interactive, educational exercise.
Our esteemed panelists will initiate the session with a lively discussion on the exponential impact of AI/ML advancements on cyberattacks and defense across all industries. Explore how the increased acceleration of automation, sophisticated evasion techniques, faster and precise attacks, scalability, and advanced analysis and response capabilities are shaping cybersecurity in diverse sectors. Gain valuable insights into the government’s role in AI and its implications for safeguarding against cyberthreats in various industries.
Following the panel discussion, we will transition into an interactive session where audience volunteers will join the panelists onstage to participate in a thought-provoking and exciting session of cybersecurity, “This or That.”
This session is designed to provide both panelists and the audience with a friendly and enriching experience, enabling you to enhance your understanding of AI/ML complexity and explore effective strategies.
Don’t miss out on this unique opportunity to learn, engage and have fun!
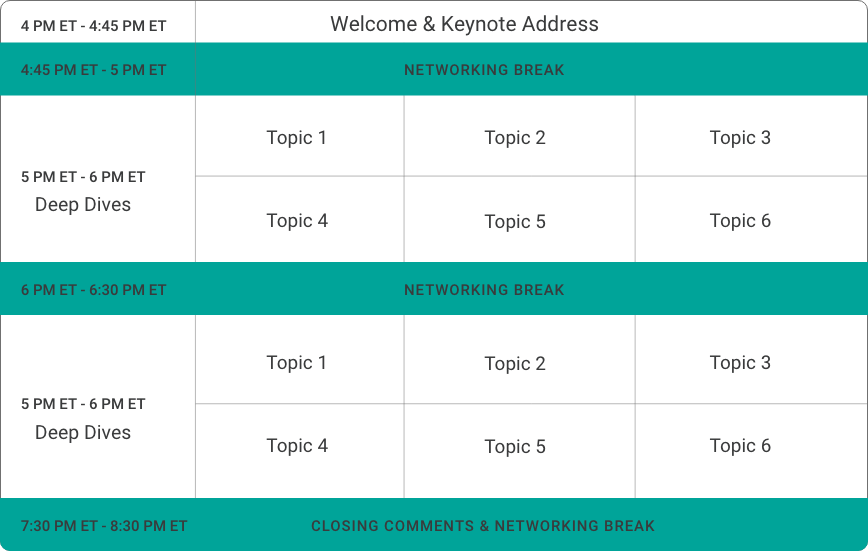
4:00 pm – 4:45 PM PT
In a digital first age, make personal and profound connections with fellow leading security experts, business leaders and practitioners to exchange real-world insights.
4:45 pm et – 5:00 pm Pt & 6:00 pm et – 6:30 pm Pt
Meet with security industry leaders in a boardroom setting to converse with peers and gain insight into leading security trends and technology. Participate in two of the following topic-based closed door Deep Dive Discussions.
However they often struggle to understand threats and translate them into actionable countermeasures.
High quality defensive knowledge is scarce, and adversaries continue to take advantage of weak points including misconfigured defenses, poor security architectures, and excessive privileges, further reducing the value of investment in security solutions.
Discussion topics will explore:
Provide insights on how to improve resiliency and mitigate impact of attacks
Session 1 – 5:00 PM pt – 6:00 PM pt Session 2 – 6:30 PM pt – 7:30 PM pt
The SASE (secure access service edge) model enables this transformation by leveraging the power of the public cloud to simultaneously improve security and user experience. A well architected SASE approach can help organizations accelerate their digital journey by consistently applying zero trust policies for all users, applications and devices, no matter where they may be located.
Gartner forecasts that SASE will be a $15 billion market in Asia-Pacific and Japan by 2025. However, with all the market noise around SASE, it is hard to differentiate between hype and practical outcomes and strategies. But questions remain: What is the business value of a SASE strategy? How to communicate the SASE strategy to the business and board of directors?
Discussion topics will explore:
Session 1 – 5:00 PM pt – 6:00 PM pt Session 2 – 6:30 PM pt – 7:30 PM pt
A potential lack of visibility into apps, users and network traffic, coupled with alert fatigue, means practitioners may need a clearer view of their environment – before low-and-slow network reconnaissance leads to a potential crypto-locking nightmare. As enterprises mature in the cloud and their technology stacks grow – it becomes increasingly important to quickly detect and respond to vulnerabilities, malware and compromised assets. Network defenders, then, must use “contextual risk” factors to determine their next action items.
Discussion topics will explore:
Session 1 – 5:00 PM pt – 6:00 PM pt Session 2 – 6:30 PM pt – 7:30 PM pt
Since then, that record has been crushed, and adversaries continue to leverage DDoS attacks for distraction, destruction and as companions to ransomware campaigns.
What are the top trends in both application-layer and network-layer DDoS attacks? What are the ransom attack trends? What are the five critical considerations for mitigating modern DDoS attacks?
Discussion Points will explore:
Session 1 – 5:00 PM pt – 6:00 PM pt Session 2 – 6:30 PM pt – 7:30 PM pt
Specifically, executives believe that security (75%) and compliance (76%) requirements hinder innovation. Catching problems early and fixing them before they slow the process or get into production is still the ultimate goal of shift left. However, a new approach and mindset are required to deliver on the promise.
Discussion topics will explore:
Session 1 – 5:00 PM pt – 6:00 PM pt Session 2 – 6:30 PM pt – 7:30 PM pt
7:30 pm pt – 8:00 pm pt
#ISMGEngage
@ISMG_News



Join like-minded cybersecurity professionals ready to learn from an industry keynote and share their thoughts and opinions during the Deep Dive sessions. Hear from your peers and interact with others that face the same day-to-day challenges as you.
Engage offers Continuing Education Credits. Learn informative and engaging content created specifically for security professionals.